● Fortinet NSE 7 - OT Security 7.2 Exam Materials
The Actual questions for Fortinet NSE 7 - OT Security 7.2. (NSE7_OTS-7.2) - Updated Weekly
Question #1

Question #2
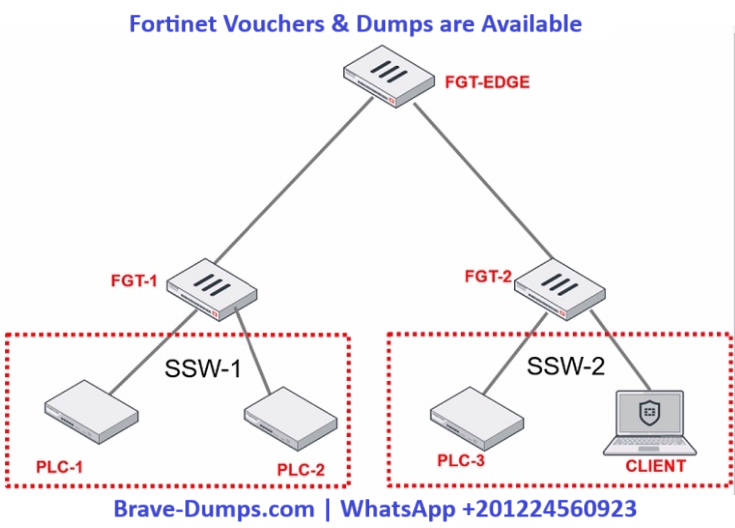
Refer to the exhibit.
PLC-3 and CLIENT can send traffic to PLC-1 and PLC-2. FGT-2 has only one software switch (SSW-2) connecting both PLC-3 and CLIENT. PLC-3 and CLIENT can send traffic to each other at the layer 2 level.
What must the operational technology (OT) admin do to prevent layer 2-level communication between PLC-3 and CLIENT?
(Choose one answer)
- A. Create a VLAN for each device and replace the current FGT-2 software switch members.
- B. Enable an explicit intra-switch policy to require firewall policies on FGT-2.
- C. Implement policy routes on FGT-2 to control traffic between devices.
- D. Set a unique forward domain for each interface of the software switch.
Question #3
The operational technology (OT) network analyst runs different levels of reports to investigate threats that exploit the network. The analyst can run these reports on all routers, switches, and firewalls.
Which FortiSIEM reporting method can analysts use to identify threats that exploit image firmware files?
(Choose one answer)
- A. Threat hunting reports
- B. Payment card industry (PCI) logging reports
- C. Compliance reports
- D. Configuration management database (CMDB) reports
Question #4
Which two statements about the Modbus protocol are true? (Choose two answers)
- A. Modbus is used to establish communication between intelligent devices
- B. Most of the PLC brands come with a built-in Modbus module
- C. Modbus uses UDP frames to transport MBAP and function codes
- D. You can implement Modbus networking settings on internetworking devices
Question #5
An OT network architect must deploy a solution to protect fuel pumps in an industrial remote network. All the fuel pumps must be closely monitored from the corporate network for any temperature fluctuations.
How can the OT network architect achieve this goal?
(Choose one answer)
- A. Configure a fuel server on the remote network, and deploy a FortiSIEM with a single pattern temperature security rule on the corporate network.
- B. Configure a fuel server on the corporate network, and deploy a FortiSIEM with a single pattern temperature performance rule on the remote network.
- C. Configure a fuel server on the remote network, and deploy a FortiSIEM with a single pattern temperature performance rule on the corporate network.
- D. Configure both fuel server and FortiSIEM with a single-pattern temperature performance rule on the corporate network.
Question #6
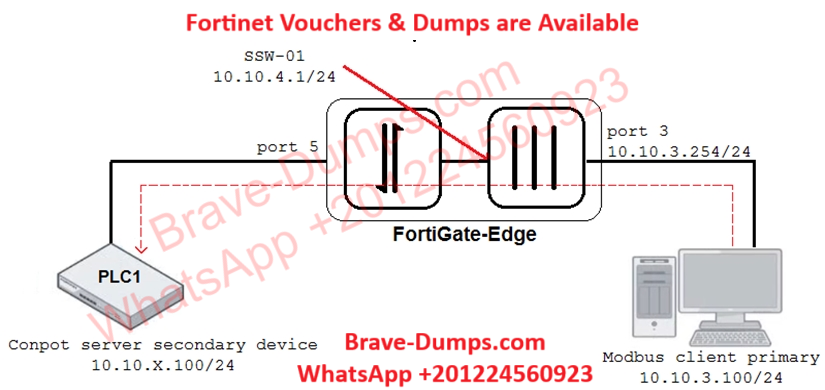
Refer to the exhibit.
An OT architect has implemented a Modbus TCP with a simulation server Conpot to identify and control the Modus traffic in the OT network. The FortiGate-Edge device is configured with a software switch interface ssw-01.
Based on the topology shown in the exhibit, which two statements about the successful simulation of traffic between client and server are true?
(Choose two answers)
- A. The FortiGate-Edge device must be in NAT mode.
- B. NAT is disabled in the FortiGate firewall policy from port3 to ssw-01.
- C. The FortiGate devices is in offline IDS mode.
- D. Port5 is not a member of the software switch.
Question #7
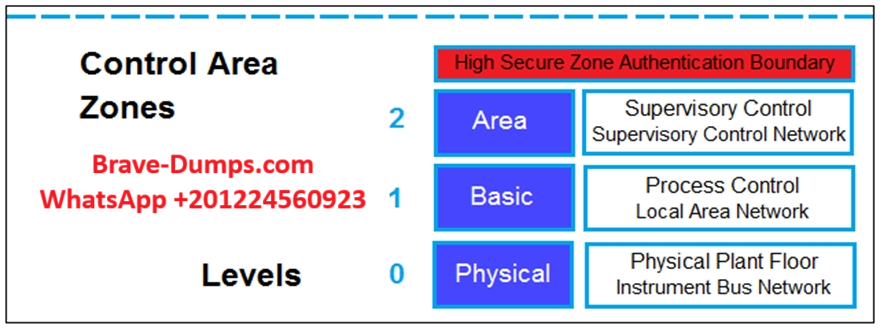
Refer to the exhibit.
Based on the Purdue model, which three measures can be implemented in the control area zone using the Fortinet Security Fabric?
(Choose three answers)
- A. FortiGate for SD-WAN
- B. FortiGate for application control and IPS
- C. FortiNAC for network access control
- D. FortiSIEM for security incident and event management
- E. FortiEDR for endpoint detection
Question #8
When device profiling rules are enabled, which devices connected on the network are evaluated by the device profiling rules? (Choose one answer)
- A. Known trusted devices, each time they change location
- B. All connected devices, each time they connect
- C. Rogue devices, only when they connect for the first time
- D. Rogue devices, each time they connect
Question #9
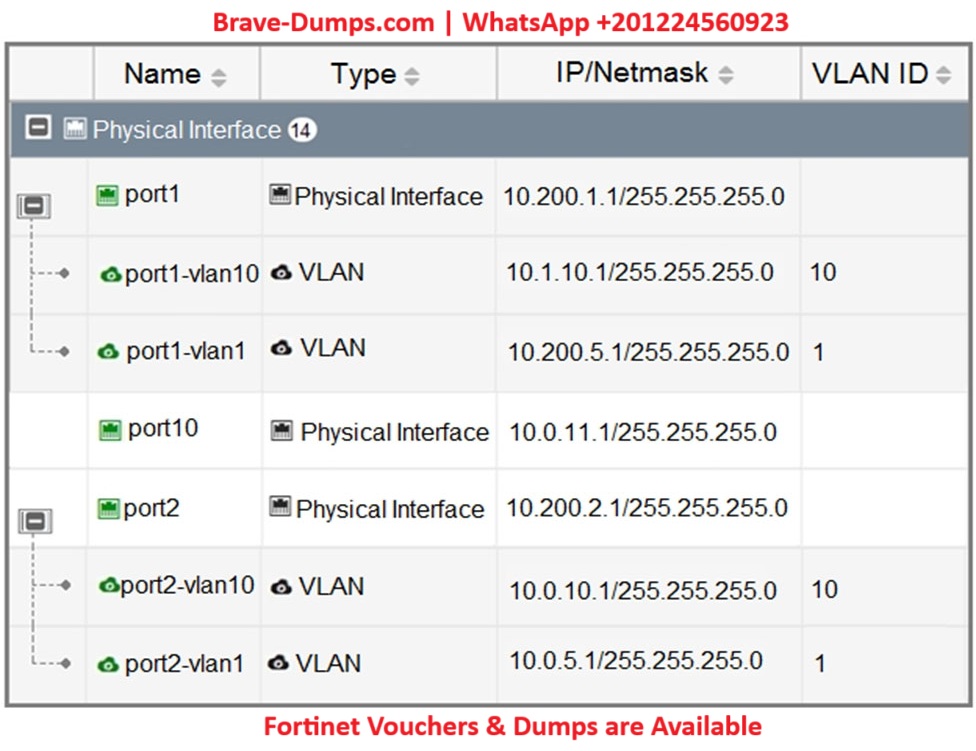
Refer to the exhibit.
Which statement about the interfaces shown in the exhibit is true?
(Choose one answer)
- A. port2, port2-vlan10, and port2-vlan1 are part of the software switch interface.
- B. The VLAN ID of port1-vlan1 can be changed to the VLAN ID 10.
- C. port1-vlan10 and port2-vlan10 are part of the same broadcast domain
- D. port1, port1-vlan10, and port1-vlan1 are in different broadcast domains
Question #10
When you create a user or host profile; which three criteria can you use? (Choose three answers)
- A. An applied (existing) access policy
- B. Administrative group membership
- C. Location
- D. Host or user group memberships
- E. Host or user attributes
Refer to the exhibit.
An OT administrator ran a report to identify device inventory in an OT network.
Based on the report results, which report was run? (Choose one answer)