● FCP - FortiWeb 7.4 Administrator Exam Materials
The Actual questions for FCP - FortiWeb 7.4 Administrator (FCP_FWB_AD-7.4) - Updated Weekly
Question #1
Question #2
Which three security features must you configure on FortiWeb to protect API connections? (Choose three answers)
- A. API user key enforcement
- B. Single sign-on (SSO) authentication with Active Directory (AD)
- C. Machine learning (ML)-based API protection
- D. API schema validation
- E. API user authentication with SAML
Question #3
In SAML deployments, which server contains user authentication credentials (username/password)? (Choose one answer)
- A. Identity provider
- B. Service provider
- C. User database
- D. Authentication client
Question #4
Which is an example of a cross-site scripting (XSS) attack? (Choose one answer)
- A. SELECT username FROM accounts WHERE username='admin';-- ' AND password='password';
- B. <img src="http://badfile/nothere" onerror=alert(document.cookie);>
- C. SELECT username FROM accounts WHERE username='XSS' ' AND password='alert("http://badurl.com")';
- D. <IMG SRC="xss.png">
Question #5
An administrator notices multiple IP addresses attempting to log in to an application frequently, within a short time period.
They suspect attackers are attempting to guess user passwords for a secure application.
What is the best way to limit this type of attack on FortiWeb, while still allowing legitimate traffic through?
(Choose one answer)
- A. Blocklist any suspected IPs.
- B. Configure a brute force login custom policy.
- C. Rate limit all connections from suspected IP addresses.
- D. Block the IP address at the border router.
Question #6
What are two possible impacts of a DoS attack on your web server? (Choose two answers)
- A. The web application starts accepting unencrypted traffic.
- B. The web application is unable to accept any more connections because of network socket exhaustion.
- C. The web application server is unable to accept new client sessions due to memory exhaustion.
- D. The web application server database is compromised with data theft.
Question #7
Which three stages are part of creating a machine learning (ML) bot detection algorithm? (Choose three answers)
- A. Model building
- B. Model running
- C. Model verification
- D. Sample collecting
- E. Model Bayesian analysis
Question #8
Which two items can be defined in a FortiWeb XML Protection Rule? (Choose two answers)
- A. API key
- B. XML Schema
- C. Web protection profile
- D. Request URL
Question #9
What are two results of enabling monitor mode on FortiWeb? (Choose two answers)
- A. It does not affect denial-of-service (DoS) protection profile actions to rate limit traffic.
- B. It uses the default action for all profiles and, depending on the configuration, blocks or allows traffic.
- C. It does not affect any HTML rewriting or redirection actions in web protection profiles.
- D. It overrides all usual profile actions. FortiWeb accepts all requests and generates alert email or log messages only for violations.
Question #10
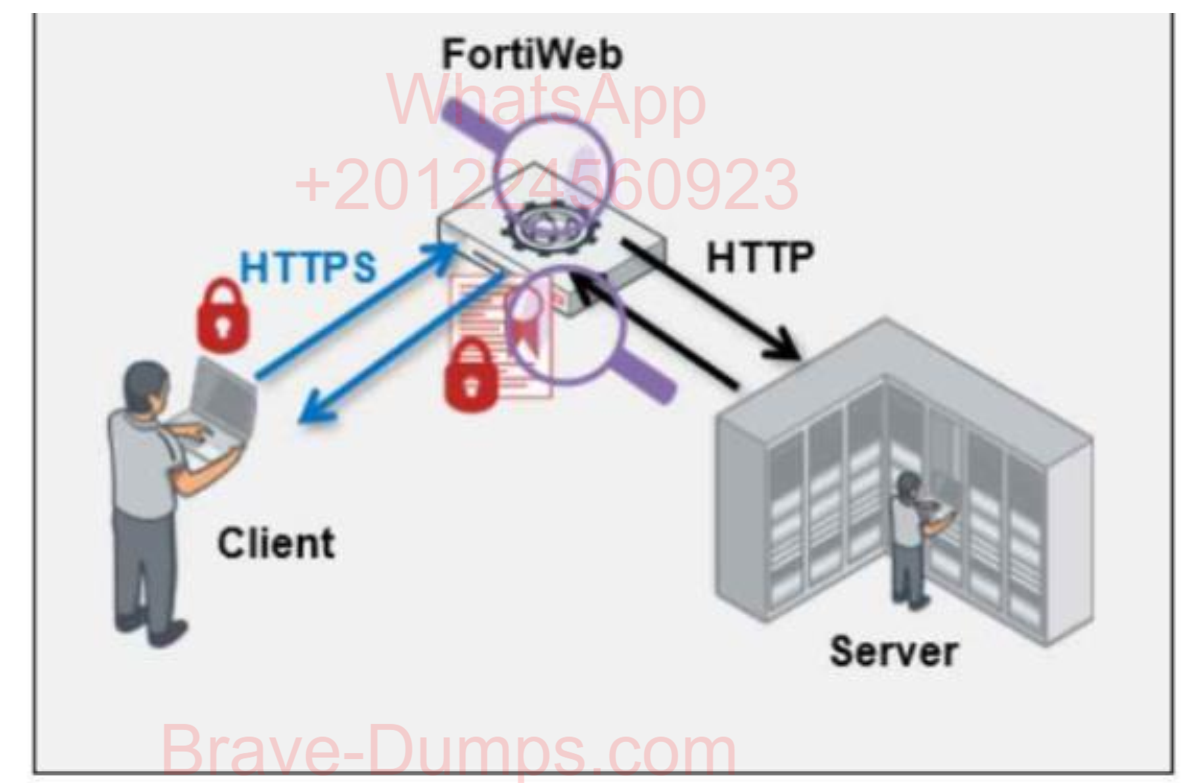
Refer to the exhibits.
Which statement is true?
(Choose one answer)
- A. FortiWeb cannot perform content inspection on the traffic because it is encrypted.
- B. FortiWeb is decrypting and re-encrypting the traffic.
- C. The server is not performing any cryptography on the traffic.
- D. The server is encrypting traffic being sent to the client.
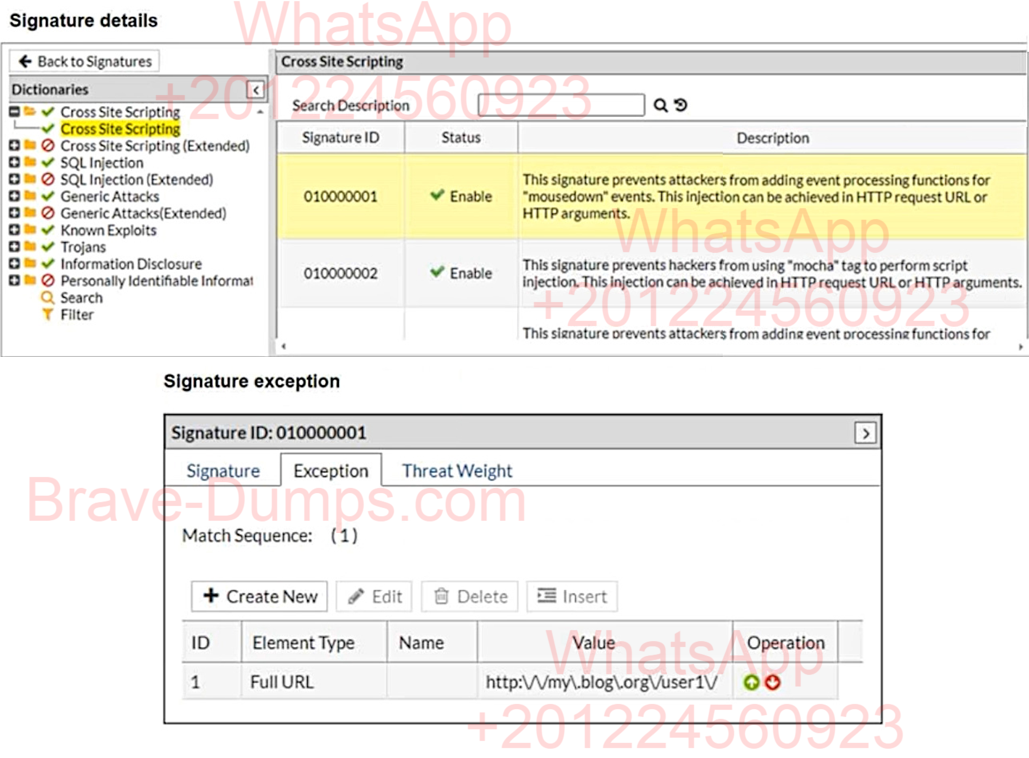
Refer to the exhibits.
What will happen when a client attempts a mousedown cross-site scripting (XSS) attack against the site http://my.blog.org/userl1/blog.php and FortiWeb is enforcing the highlighted signature? (Choose one answer)