● FCP - FortiMail 7.4 Administrator Exam Materials
The Actual questions for FCP - FortiMail 7.4 Administrator (FCP_FML_AD-7.4) - Updated Weekly
Question #1
Question #2
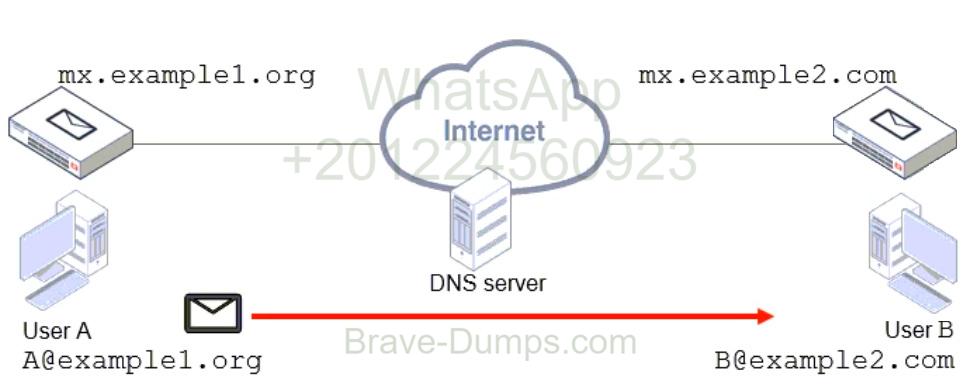
Refer to the exhibit, which shows a topology diagram of two separate email domains.
Which two statements correctly describe how an email message is delivered from User A to User B?
(Choose two answers)
- A. mx.example1.org will forward the email message to the MX record that has the lowest preference.
- B. User B will retrieve the email message using either POP3 or IMAP.
- C. User A’s MUA will perform a DNS MX record lookup to send the email message.
- D. The DNS server will act as an intermediary MTA.
Question #3
Refer to the exhibit, which shows a topology diagram of a FortiMail cluster deployment.
Which IP address must the DNS MX record for this organization resolve to?
(Choose one answer)
- A. 172.16.32.57
- B. 172.16.32.1
- C. 172.16.32.56
- D. 172.16.32.55
Question #4
Which two factors are required for an active-active HA configuration of FortiMail in server mode? (Choose two answers)
- A. A primary must be designated to initially process email.
- B. Mail data must be stored on a NAS server.
- C. Service monitoring must be configured for remote SMTP.
- D. Devices must be deployed behind a load balancer.
Question #5
A FortiMail device is configured with the protected domain example.com.
If none of the senders is authenticated, which two envelope addresses will require an access receive rule?
(Choose two answers)
- A. MAIL FROM: [email protected] RCPT TO: [email protected]
- B. MAIL FROM: [email protected] RCPT TO: [email protected]
- C. MAIL FROM: [email protected] RCPT TO: [email protected]
- D. MAIL FROM: [email protected] RCPT TO: [email protected]
Question #6
A FortiMail administrator is concerned about cybercriminals attempting to get sensitive information from employees using phishing attacks.
Which option can the administrator configure to prevent these types of attacks?
(Choose one answer)
- A. Impersonation analysis
- B. Dictionary profile with predefined smart identifiers
- C. Bounce tag verification
- D. Content disarm and reconstruction
Question #7
Which item is a supported one-time secure token for IBE authentication? (Choose one answer)
- A. FortiToken
- B. SMS
- C. Security question
- D. Certificate
Question #8
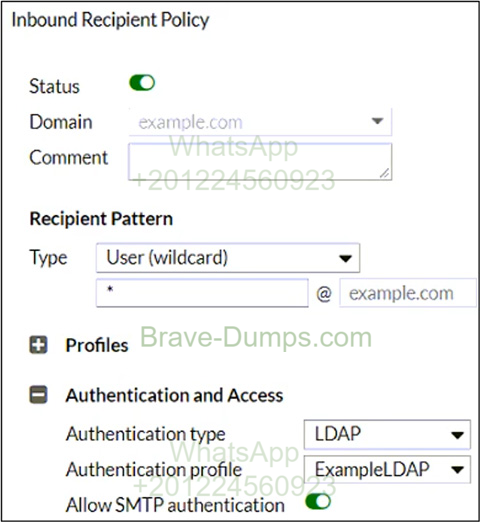
Refer to the exhibit, which shows an inbound recipient policy.
After creating the policy shown in the exhibit, an administrator discovers that clients can send unauthenticated emails using SMTP.
What must the administrator do to enforce authentication?
(Choose one answer)
- A. Configure an access receive rule to verify authentication status.
- B. Configure an outbound recipient policy for LDAP authentication.
- C. Configure an access delivery rule to enforce authentication.
- D. Configure a matching IP policy with the exclusive flag enabled.
Question #9
What are two disadvantages of configuring the dictionary and DLP scan rule aggressiveness too high? (Choose two answers)
- A. It is more resource intensive.
- B. More false positives could be detected.
- C. FortiMail requires more disk space for the additional rules.
- D. High aggressiveness scan settings do not support executable file types.
Question #10
An administrator wants to provide an administratively managed address book to all users in a multidomain FortiMail deployment.
Which type of address book must they create?
(Choose one answer)
- A. Domain
- B. Global
- C. System
- D. Personal
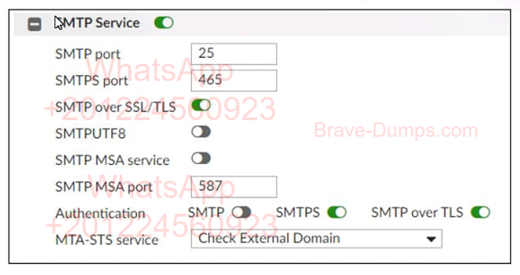
Refer to the exhibit,
which displays the Mail Settings page of a FortiMail device running in gateway mode.
In addition to selecting Check External Domain in the MTA-STS service field, what else must an administrator do to enable MTA-STS? (Choose one answer)