● FCP - FortiGate 7.4 Administrator Exam Materials
Please note that the exam "FCP - FortiGate 7.4 Administrator Exam " is no longer offered by Fortinet and is not available for booking through Pearson VUE, so we opened it on free view,
It has been replaced by the exam "NSE 4 - FortiOS 7.6 Exam"
The new exam version is available on Brave-Dumps and can be purchased.
It has been replaced by the exam "NSE 4 - FortiOS 7.6 Exam"
The new exam version is available on Brave-Dumps and can be purchased.
Question #1
Question #2
An administrator manages a FortiGate model that supports NTurbo.
How does NTurbo enhance performance for flow-based inspection?
(Choose one answer)
- A. NTurbo creates two inspection sessions on the FortiGate device.
- B. NTurbo offloads traffic to the content processor.
- C. NTurbo creates a special data path to redirect traffic between the IPS engine its ingress and egress interfaces.
- D. NTurbo buffers the whole file and then sends it to the antivirus engine.
Question #3
Which two statements about equal-cost multi-path (ECMP) configuration on FortiGate are true? (Choose two answers)
- A. If SD-WAN is disabled, you can configure the parameter v4-ecmp-mode to volume-based.
- B. If SD-WAN is enabled, you control the load balancing algorithm with the parameter load-balance-mode.
- C. If SD-WAN is disabled, you configure the load balancing algorithm in config system settings.
- D. If SD-WAN is enabled, you can configure routes with unequal distance and priority values to be part of ECMP.
Question #4
A FortiGate firewall policy is configured with active authentication, however, the user cannot authenticate when accessing a website.
Which protocol must FortiGate allow even though the user cannot authenticate?
(Choose one answer)
- A. DHCP
- B. DNS
- C. ICMP
- D. LDAP
Question #5
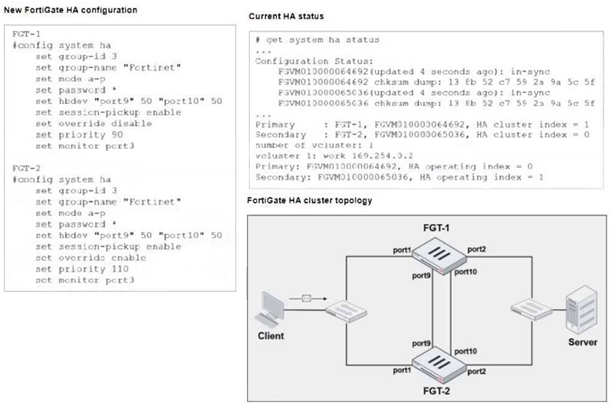
Refer to the exhibits.
FGT1 and FGT2 are updated with HA configuration commands shown in the exhibit.
What would be the expected outcome in the HA cluster
(Choose one answer)
- A. FGT-1 will remain the primary because FGT-2 has lower priority
- B. B. FGT-2 will take over as the primary because it has the override enable setting and higher priority than FGT-1.
- C. FGT-1 will synchronize the override disable setting with FGT-2
- D. The HA cluster will become out of sync because the override setting must match on all HA members
Question #6
Which three strategies are valid SD-WAN rule strategies for member selection? (Choose three answers)
- A. Best Quality with load balancing
- B. Manual with load balancing
- C. Lowest Quality (SLA) with load balancing
- D. Lowest Cost (SLA) without load balancing
- E. Lowest Cost (SLA) with load balancing
Question #7
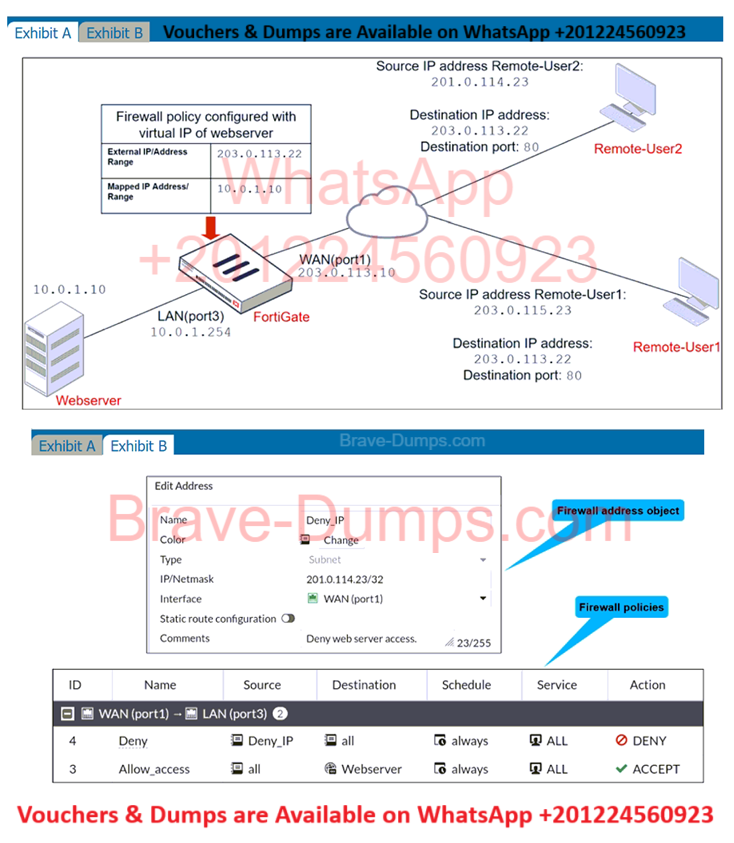
Refer to the exhibits.
The exhibits show a diagram of a FortiGate device connected to the network, and the firewall configuration.
An administrator created a Deny policy with default settings to deny Webserver access for Remote-User2.
The policy should work such that Remote-User1 must be able to access the Webserver while preventing Remote-User2 from accessing the Webserver.
Which two configuration changes can the administrator make to the policy to deny Webserver access for Remote-User2?
(Choose two answers)
- A. Enable match-vip in the Deny policy
- B. Set the Destination address as Webserver in the Deny policy
- C. Disable match-vip in the Deny policy
- D. Set the Destination address as Deny_IP in the Allow_access policy
Question #8
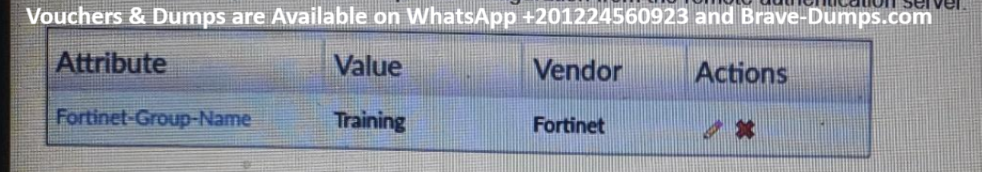
Refer to the exhibit, which shows a partial configuration from the remote authentication server.
Why does the FortiGate administrator need this configuration?
(Choose one answer)
- A. To set up a RADIUS server Secret
- B. To authenticate and match the Training OU on the RADIUS server
- C. To authenticate only the Training user group
- D. To authenticate Any FortiGate user groups
Question #9
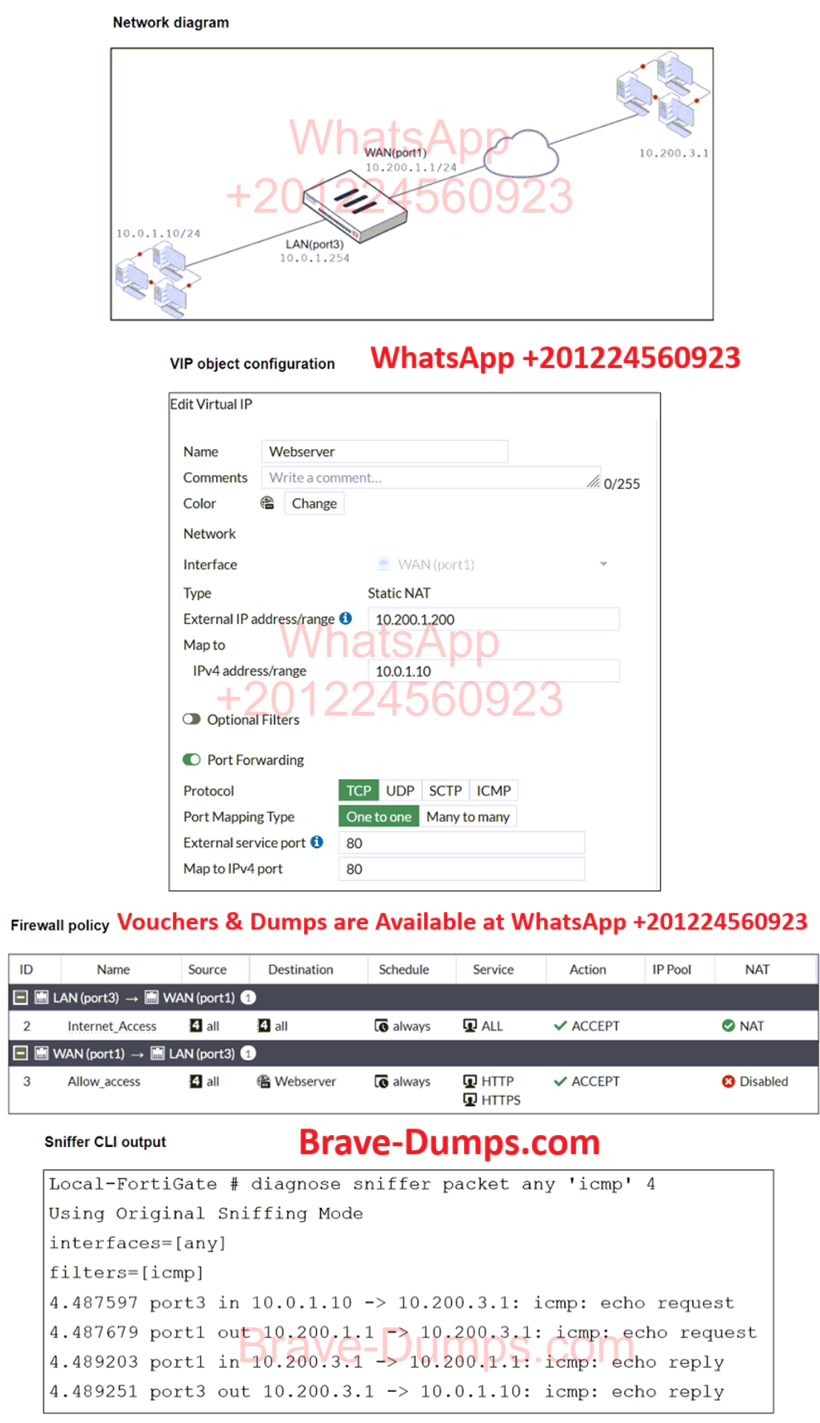
Refer to the exhibits.
The exhibits show a diagram of a FortiGate device connected to the network, VIP configuration, firewall policy, and the sniffer CLI output on the FortiGate device.
The WAN (port1) interface has the IP address 10.200.1.1/24.
The LAN (port3) interface has the IP address 10.0.1.254/24.
The webserver host (10.0.1.10) must use its VIP external IP address as the source NAT (SNAT) when it pings remote server (10.200.3.1).
Which two statements are valid to achieve this goal?
(Choose two answers)
- A. Create a new firewall policy before Internet_Access for the webserver and apply the IP pool
- B. Disable port forwarding on the VIP object
- C. Disable NAT on the Internet_Access firewall policy
- D. Enable NAT on the Allow_access firewall policy
Question #10
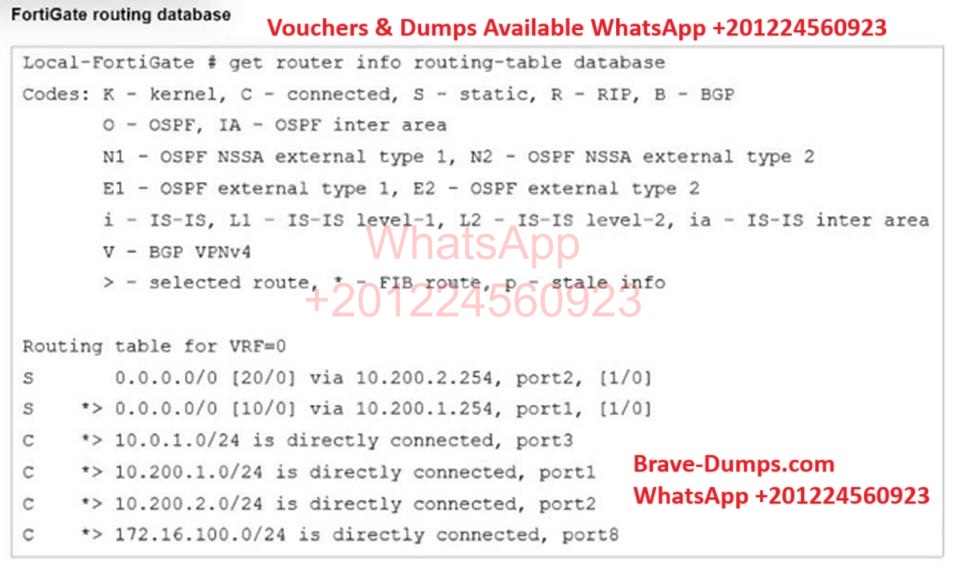
Refer to the exhibit.
Which two statements are true about the routing entries in this database table?
(Choose two answers)
- A. All of the entries in the routing database table are installed in the FortiGate routing table
- B. The port2 interface is marked as inactive
- C. Both default routes have different administrative distances
- D. The default route on port2 is marked as the standby route
A network administrator has configured an SSL/SSH inspection profile defined for full SSL inspection and set with a private CA certificate. The firewall policy that allows the traffic uses this profile for SSL inspection and performs web filtering. When visiting any HTTPS websites, the browser reports certificate warning errors.
What is the reason for the certificate warning errors? (Choose one answer)